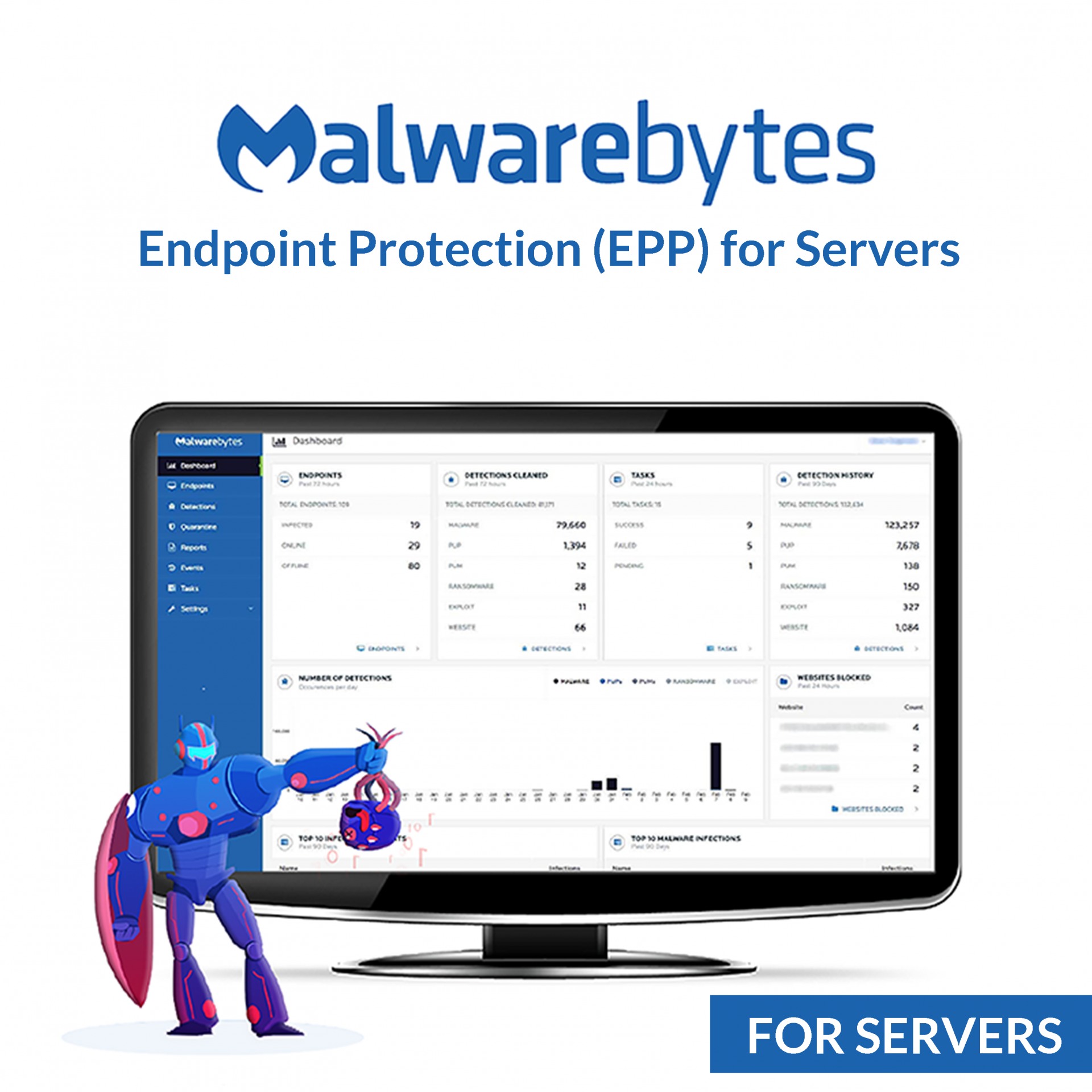
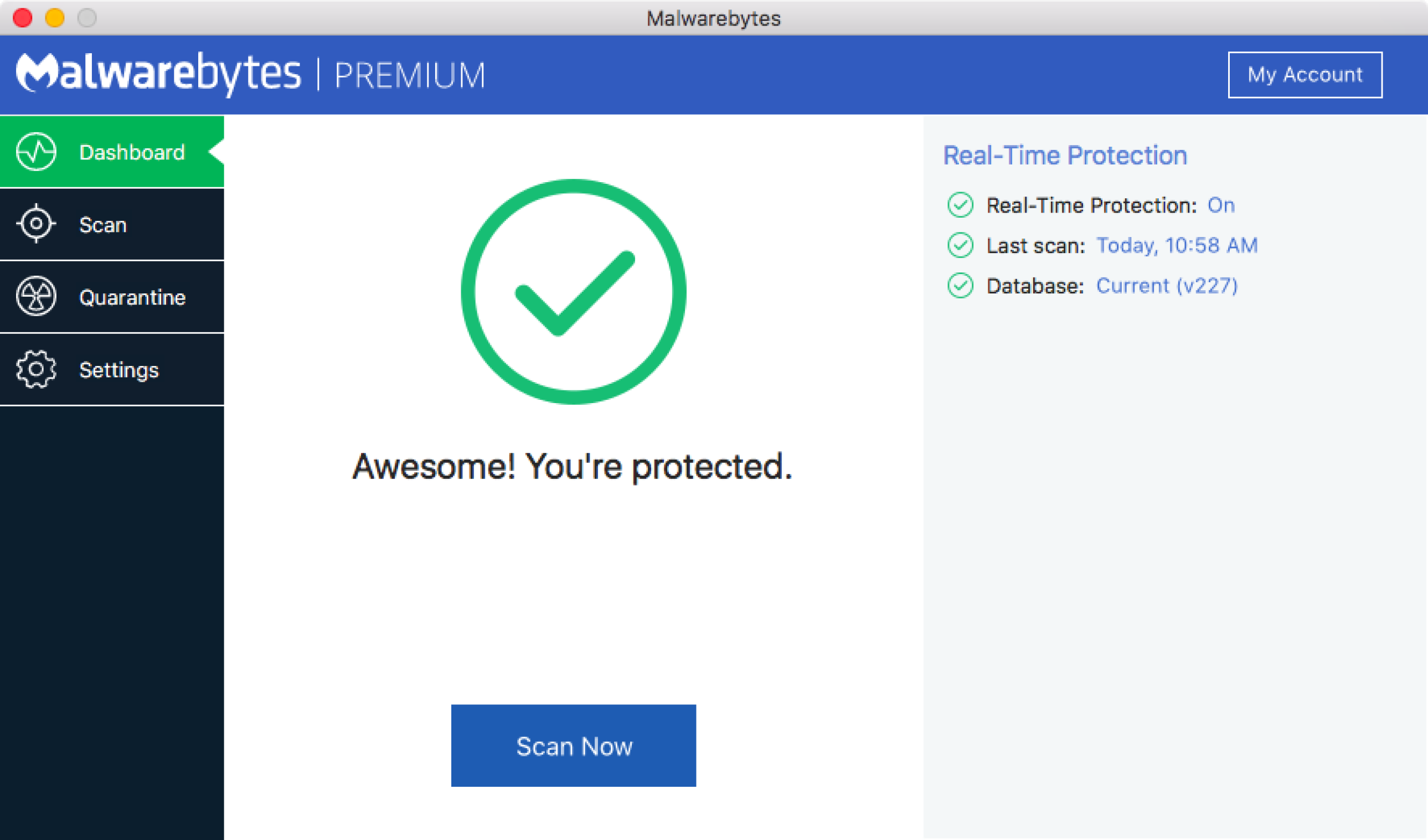
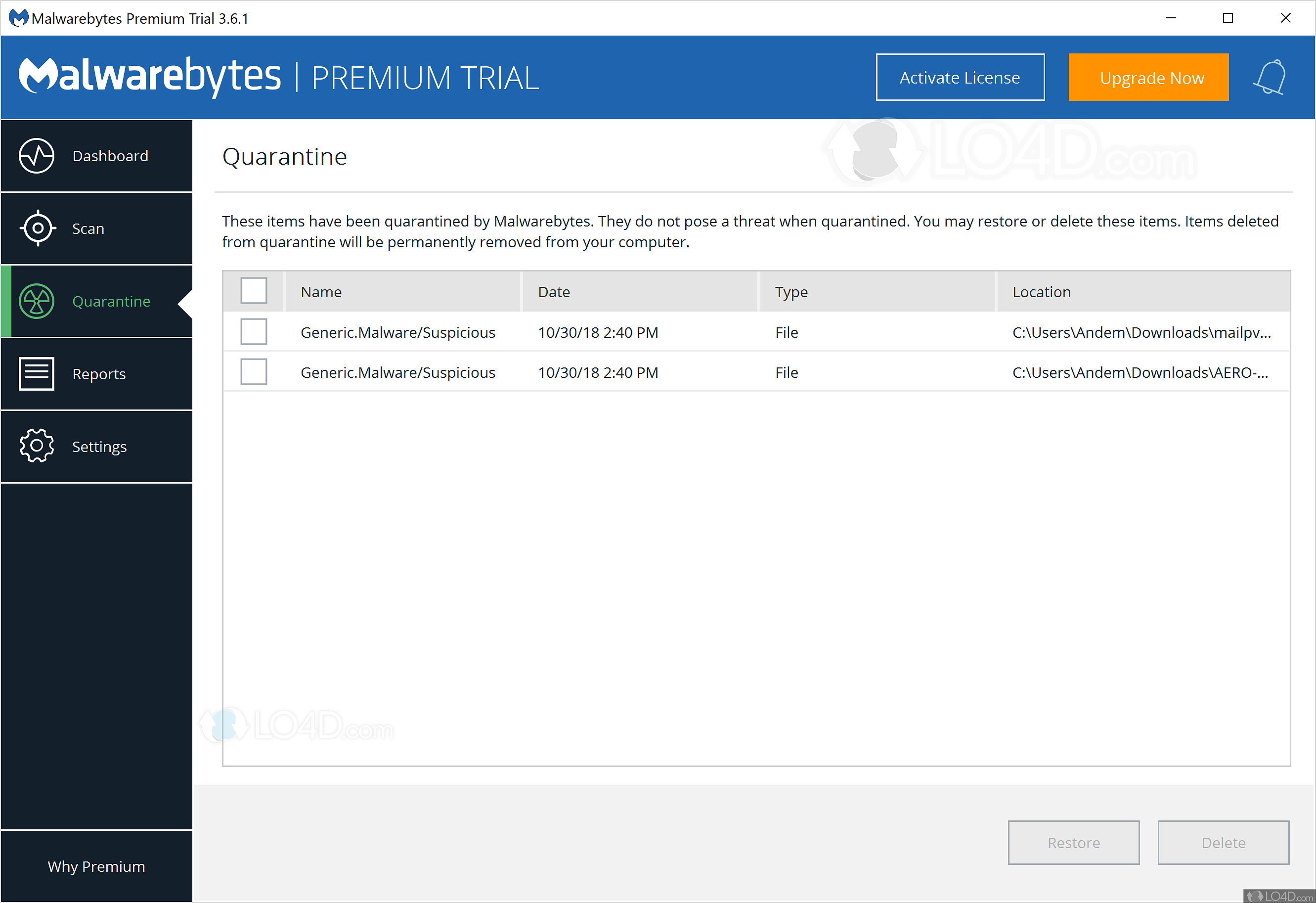
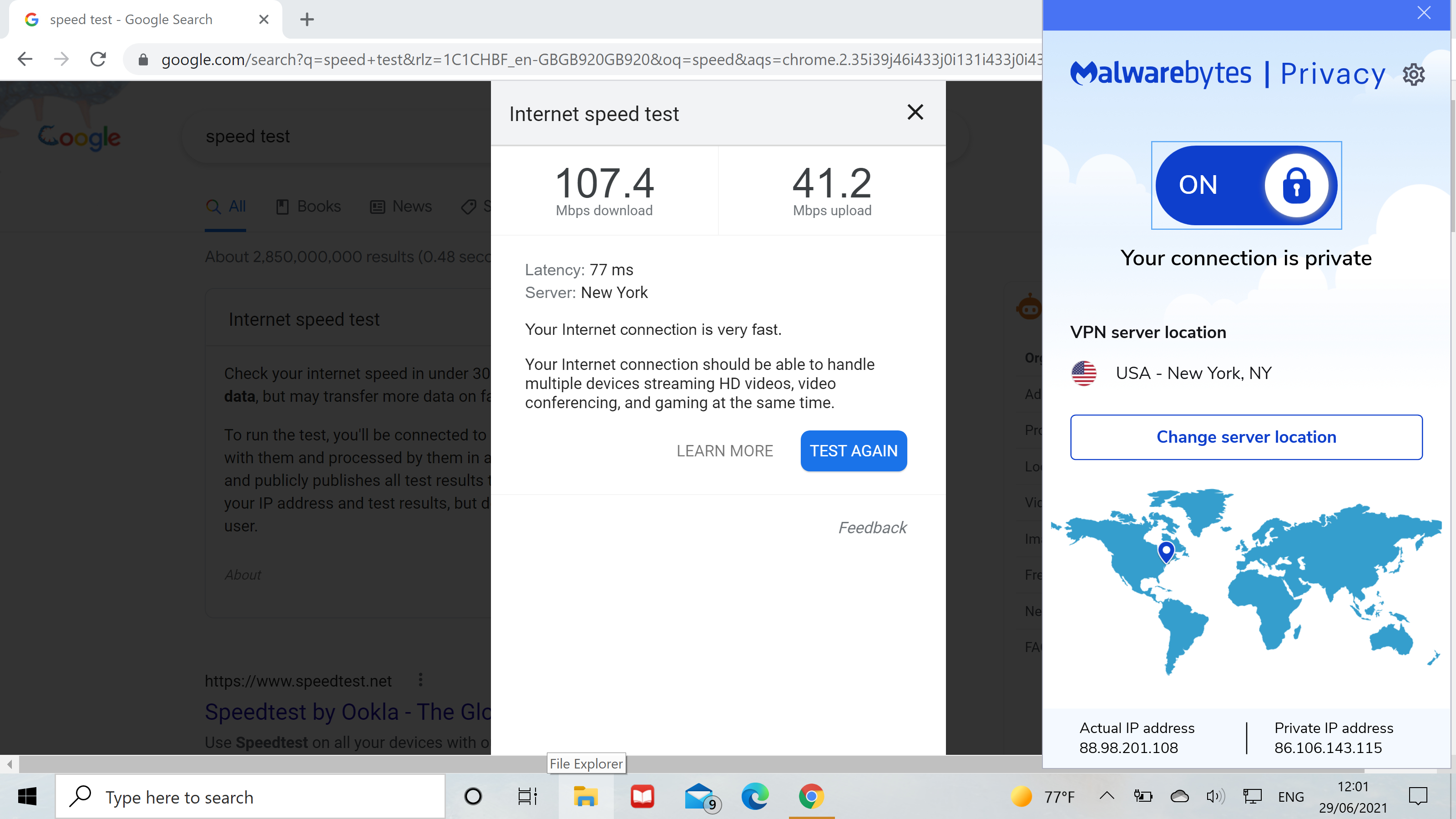
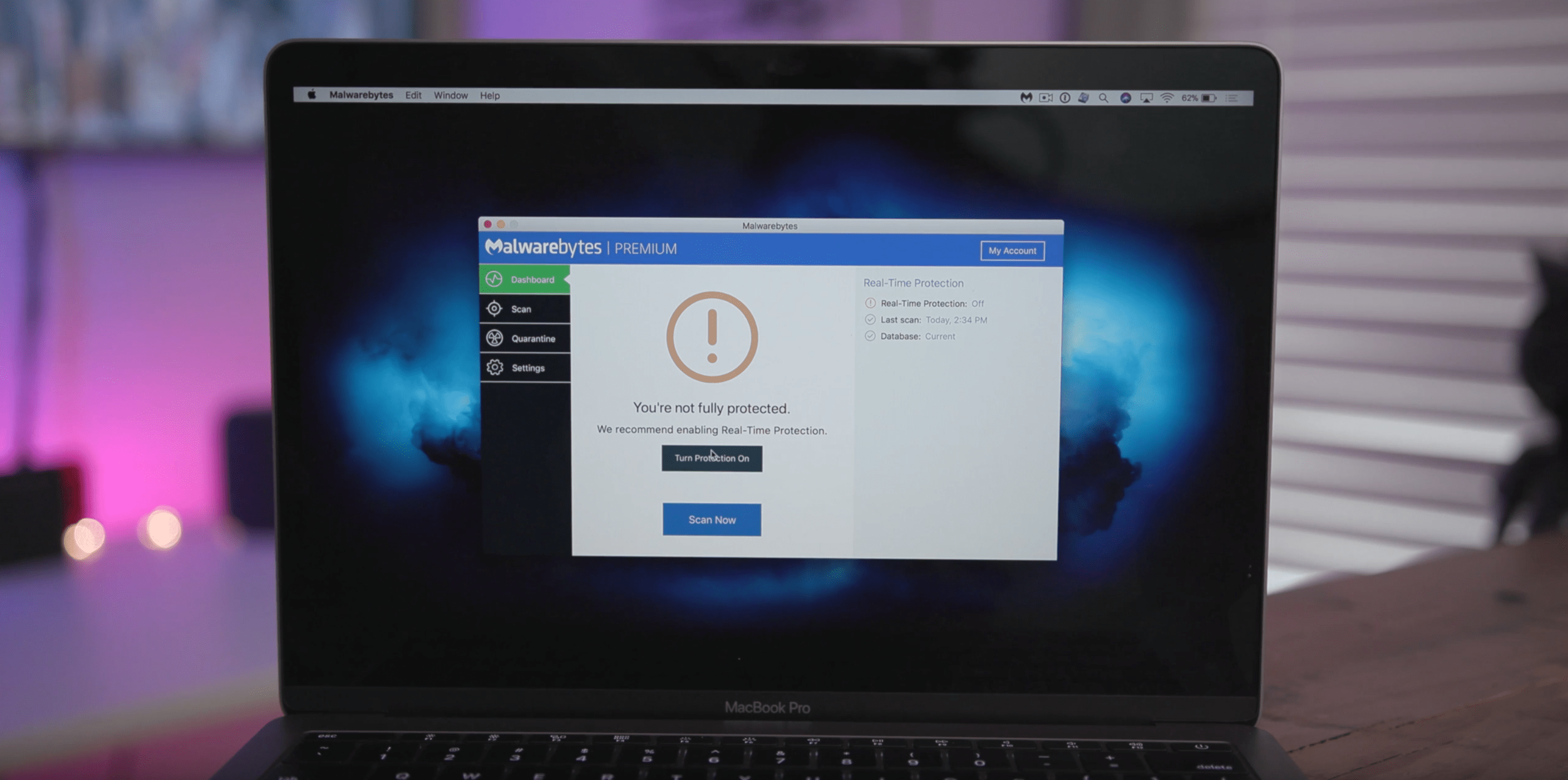
Dec 19, 2024 · more and more, threat actors are leveraging the browser to deliver malware in ways that can evade detection from antivirus programs.
How Malwarebytes Protects Against Erothoots.Com
Dec 19, 2024 · more and more, threat actors are leveraging the browser to deliver malware in ways that can evade detection from antivirus programs....